Data privacy and compliance in higher education
Introduction
Context and importance of data privacy in higher education
Higher education institutions manage vast volumes of personal data, from student records to faculty information, research data, and auxiliary services. Protecting this information is essential not only to comply with laws but to maintain trust with students, staff, and partners. A robust privacy posture supports academic freedom, enables data-driven innovation, and mitigates risk from cyber threats and reputational harm. As campuses increasingly rely on digital systems, privacy controls must be integrated into everyday processes rather than treated as an afterthought.
What this guide covers
This guide outlines key concepts, roles, and practices for achieving data privacy and regulatory compliance in higher education. It covers the regulatory landscape, governance and accountability, data collection and retention, security and breach response, privacy by design, third‑party risk, rights management, international data transfers, awareness and culture, audits, and a practical implementation roadmap. The aim is to provide a clear, actionable framework that universities and colleges can adapt to their local context.
Regulatory landscape
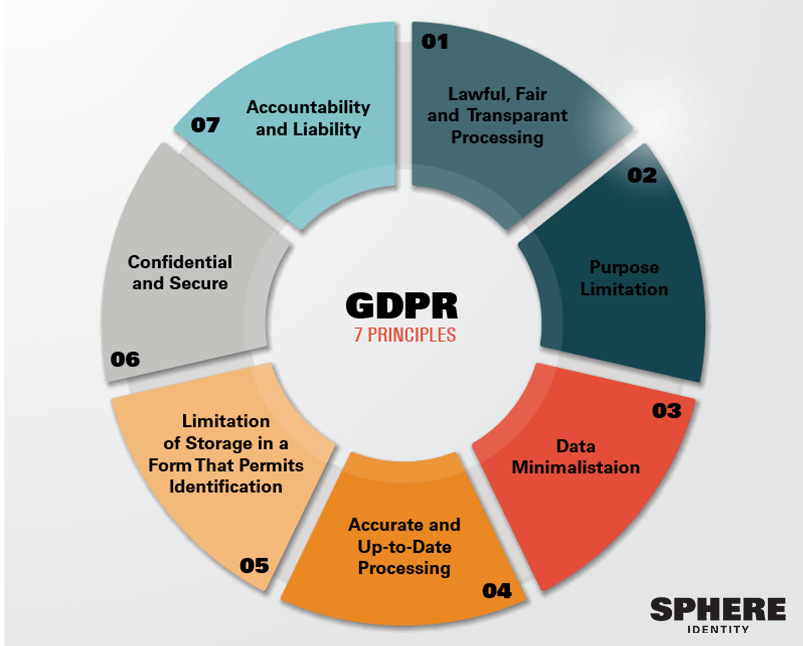
Major laws and standards (GDPR, FERPA, etc.)
Institutions operating in multiple jurisdictions must navigate a mix of laws and standards. The European Union’s General Data Protection Regulation (GDPR) emphasizes lawful processing, purpose limitation, data minimization, and transparency. In the United States, FERPA governs the privacy of student education records and interacts with state and federal requirements. Other frameworks often cited in higher education include national data protection acts, sector-specific guidelines, and international standards such as ISO 27001 for information security management. Mapping these requirements helps ensure consistent privacy controls across departments and systems.
Global vs local regulatory considerations
Global operations require harmonizing overarching principles—lawful bases for processing, consent where appropriate, and clear data subject rights—with local exceptions and carve-outs. Local privacy laws may impose stricter timelines for breach notifications, more detailed data inventories, or specific protections for particular data categories. An effective program aligns global privacy concepts with local obligations, leveraging a centralized governance model while accommodating regional nuances.
Compliance mapping and documentation
Compliance mapping involves inventorying processing activities, identifying lawful bases, documenting data flows, and recording retention schedules. A living documentation approach—data inventories, DPIAs for new projects, data processing agreements, and incident response plans—enables audit readiness and continuous improvement. Regularly reviewing mappings against changes in processes, systems, or regulations reduces the risk of gaps and drift.
Governance and roles
Data protection officer responsibilities
The data protection officer (DPO) role, when required or advisable, provides expert oversight of privacy compliance. Responsibilities typically include monitoring regulatory changes, supervising DPIAs, advising on high-risk processing, coordinating training, and acting as a liaison with supervisory authorities. The DPO should operate with independence, sufficient authority, and adequate resources to fulfill their duties.
Governance structures and policies
Effective governance combines board-level sponsorship with operational policies. Key elements include a privacy policy, data handling standards, incident response procedures, vendor risk management, and a clear escalation path for privacy incidents. Governance structures should assign ownership for data categories, processing activities, and system design decisions, ensuring accountability across faculties, IT, and administration.
Data governance framework and accountability
A formal data governance framework defines data ownership, stewardship, quality, and access controls. Accountability mechanisms—such as approvals for data sharing, documented consent capture, and routine audits—help ensure that privacy requirements are embedded in both strategic planning and day-to-day operations. Regular reviews of roles and responsibilities keep the program aligned with evolving needs and regulations.
Data collection, processing, and retention
Lawful bases for processing and purpose limitation
Processing personal data in higher education should be grounded in a lawful basis, such as legitimate interests balanced against privacy rights, contract performance (enrollment or employment), compliance with legal obligations (financial aid, research funding), vital interests, or consent where appropriate. Purpose limitation requires that data collected for a stated purpose not be repurposed in ways incompatible with that purpose without a new basis or compatibility assessment.
Data minimization and retention schedules
Collect only what is necessary to fulfill a stated purpose, and retain data for as long as needed to satisfy legal, operational, or research requirements. Establish retention schedules aligned with regulatory needs, institutional policies, and archival value. Regularly review data holdings to prune outdated or redundant information and implement automatic deletion or anonymization where feasible.
Consent management and data subject rights
When relying on consent, capture explicit, informed, and revocable consent with clear purposes. Support data subject rights such as access, correction, deletion, portability, and objection where applicable. Implement user-friendly mechanisms for individuals to exercise rights and maintain auditable records of responses and timelines.
Data security and breach response
Technical and organizational security controls
A layered security approach combines technical controls (encryption at rest and in transit, access controls, multi-factor authentication, network segmentation) with organizational measures (least privilege access, role-based training, incident management). Regular risk assessments, vulnerability management, and secure development practices strengthen resilience against threats and data exposure.
Breach notification procedures
Establish clear, legally informed procedures for identifying, assessing, and notifying stakeholders of data breaches. Documentation should specify notification timelines, required content, roles, and escalation paths. Pre-defined templates and runbooks help ensure timely and accurate communications to affected individuals and authorities where mandated.
Incident response playbooks and post-incident reviews
Develop incident response playbooks that describe detection, containment, eradication, and recovery steps. After incidents, conduct post-incident reviews to identify root causes, assess control effectiveness, and implement improvements. A culture of learning from events supports ongoing risk reduction and program maturity.
Privacy by design and DPIA
Privacy impact assessments (DPIAs) for new projects
When launching new systems, services, or data processing activities, perform DPIAs to evaluate potential privacy risks and determine mitigating controls. DPIAs should be integrated into project governance, involve stakeholders from IT, privacy, and user communities, and be revisited as projects evolve or risks change.
Integrating privacy into system design and procurement
Embed privacy requirements at the design stage of systems and during procurement. This includes specifying data minimization, access controls, data localization where appropriate, and contractually binding security obligations in vendor agreements. Privacy-by-design considerations should be a criterion in supplier selection and architectural reviews.
Third-party data sharing and vendors
Due diligence and vendor risk management
Assess vendor privacy and security capabilities before data sharing. This includes evaluating data handling practices, incident history, sub‑processor arrangements, and alignment with the institution’s risk tolerance. Ongoing vendor risk management should track changes in supplier controls and performance over time.
Data processing agreements and security clauses
Contracts with processors should specify the scope of processing, data types, retention periods, security measures, breach notification obligations, and audit rights. Include data localization and international transfer terms where applicable, ensuring conformity with applicable data protection law.
Ongoing monitoring and audits
Implement a program of continuous monitoring of vendor performance, regular security assessments, and scheduled audits. Documentation of findings and corrective actions supports accountability and demonstrates due diligence in third-party management.
Rights of students and staff
Access, correction, deletion, and portability
Provide mechanisms for individuals to access their data, request corrections, restrict or delete information where permissible, and obtain data in a structured, machine-readable format. Clear timelines and escalation paths help maintain trust and regulatory compliance.
Opt-out mechanisms and consent management
Where processing is based on consent or where individuals wish to limit certain uses, offer straightforward opt-out options. Track consent changes and ensure that future processing reflects updated preferences while preserving functional service continuity where necessary.
Handling of sensitive or special-category data
Special-category data (such as health information or biometric data) requires heightened protections, explicit consent where required, and robust controls to minimize risk. Access to such data should be tightly restricted and governed by specific policies and procedures.
International transfers and cross-border data flows
Transfer mechanisms (e.g., SCCs, adequacy decisions)
Cross-border data transfers should rely on recognized mechanisms such as standard contractual clauses (SCCs), adequacy decisions, or other lawful transfer instruments. Institutions must implement supplementary measures to address risks in the destination jurisdiction and maintain transfer documentation for audits.
Data localization considerations
Some contexts may require data localization or restricted data processing outside specific boundaries. When feasible, regional data processing can reduce cross-border complexity and enhance control over sensitive information while supporting global collaboration.
Risk assessment for cross-border processing
Assess risks associated with international transfers, including legal protections, enforcement gaps, and compliance capabilities in recipient countries. Use transfer impact assessments to inform decisions and document risk mitigation strategies.
Training, awareness, and culture
Role-based privacy training
Provide targeted training for faculty, researchers, administrative staff, and IT personnel based on their processing roles. Training should cover legal requirements, internal policies, incident reporting, and practical privacy protections integrated into daily work.
Security awareness for faculty, staff, and students
Promote a campus-wide security culture through ongoing awareness campaigns, phishing simulations, and accessible guidance on safe data handling, device security, and incident reporting. Engaging education helps create shared responsibility for privacy and safety.
Building a privacy-conscious organizational culture
A privacy-centric culture emerges from leadership example, transparent decision-making, and visible accountability. Regular communications about privacy goals, successes, and lessons learned reinforce the importance of safeguarding personal data as a core institutional value.
Audits, monitoring, and accountability
Internal and external audits
Regular audits verify compliance with policies and laws, identify gaps, and validate the effectiveness of controls. External audits provide independent assurance, while internal reviews support continuous improvement. Findings should drive concrete remediation plans and tracked progress.
KPIs, dashboards, and reporting
Define privacy and security metrics (e.g., incident response times, DPIA coverage, data subject request processing) and present them in accessible dashboards. Regular reporting to leadership and governance bodies ensures visibility and accountability across the institution.
Continuous improvement processes
Privacy programs should include feedback loops, threat and control updates, and periodic policy refreshes. Emphasize learning from incidents, regulatory changes, and evolving technology to keep controls current and effective.
Practical implementation roadmap
Phase-based rollout and milestones
Adopt a phased approach: Phase 1 focuses on foundations—policy alignment, data inventories, and core governance. Phase 2 scales privacy controls across critical systems and key processes. Phase 3 embeds privacy into operations, procurement, and ongoing improvement, with mature incident response and DPIA practices.
Maturity model and capability levels
Use a maturity model to benchmark progress across areas such as policy, governance, data handling, security, and training. Capability levels—from initial to optimized—help prioritize investments and track evolution over time.
Templates, checklists, and playbooks
Develop practical artifacts to support implementation: DPIA templates, data inventory worksheets, vendor risk questionnaires, incident response playbooks, and breach notification templates. Centralized repositories enable reuse and consistency across departments.
Key takeaway
UNESCO emphasizes protecting personal data in education while enabling access to learning. It highlights governance structures, privacy-by-design in educational technology, and capacity building to safeguard rights. The guidance supports using data for improvement without compromising student and staff privacy. For reference, see UNESCO guidance at the following source: UNESCO document.
Conclusion and next steps
Checklist of core practices
To summarize, ensure you have: a formal privacy policy and governance framework; documented data inventories and processing purposes; DPIAs for new initiatives; robust data security controls; clear incident response and breach notification procedures; strong third-party risk management; processes for data subject rights; and an ongoing training and awareness program. Establish a practical roadmap with phased milestones and measurable KPIs to guide ongoing improvement.
Resource references and further reading
Consult foundational privacy texts, national guidance, and sector-specific resources to refine your program. Key references include privacy laws and standards applicable to your jurisdiction, institutional policies, and privacy-by-design guidance that align with UNESCO’s emphasis on safeguarding rights while enabling educational access.